Wireshark 101 – Introduction
Wireshark is my favorite networking tool and I have used it pretty much on a weekly basis over the past couple of years. Not only has it saved me multiple times at work as I investigate various issues, it’s also allowed me to expand and solidify my knowledge of networking. It’s a wonderful troubleshooting tool and an invaluable learning resource. That’s why I think you should use it whether you’re already working in the networking field or learning the basics as a student.
So, what is Wireshark? Wireshark is a network packet analysis tool. That means we need to define what packets are before we can understand why analyzing them with Wireshark is helpful. Allow me to launch into a long-winded explanation. It turns out that everything your computer sends or receives across a network or the Internet is actually a stream of 1’s and 0’s. That means every picture, every streamed song, every video, and every bit of data that goes into making online computer games work are all comprised of just 1’s and 0’s and nothing more. It might seem a little implausible if you haven’t been exposed to this concept before, but it’s true. The trick is that we use a lot of 1’s and 0’s. For instance, a picture I have saved on my computer that was taken by my cellphone is made up of 2,838,456 1’s and 0’s. Programs that have the capability to render pictures on your computer are able to process that stream of nearly 3 million digits and turn it into something that’s appealing to the eyes.
Now, let’s expand our terminology a little. From now on, we’ll refer to a single 1 or a single 0 as a ‘bit’, and we’ll call any combination of 8 bits a ‘byte’. A byte is a sort of special length of bits that you will see over and over again. A byte can be any combination of bits. Each of these numbers separated by commas are examples of a byte: 00000000, 11111111, 11001100, 11110000, 10101010, 10011010, 01101010. Each of these strings of bits is a byte simply because the definition of a byte is that it is 8 bits in length. There’s also a designation for the length of 4 bits, and it is somewhat humorously referred to as a nibble (it’s half of a byte…get it?).
Groups of bytes that are sent across a computer network are referred to as packets–we finally made it to the definition of a packet, whew! Inside a packet, there may be different sections of bytes for different purposes. For instance, when downloading a picture from a website, the bytes that ultimately make up the picture itself are of course present in the packets. But there are other bytes in the packets as well, for example bytes that are used to make sure that the packet arrives at the correct location (like your computer), and bytes that are used to make sure the packets are reordered correctly once they are received (so your picture isn’t a jumbled mess of pixels). In other words, there are different layers to each packet–packets aren’t just comprised of the data they are trying to convey.
The bytes in each layer of a packet define information based on what protocol is being used at that layer. As an example, let’s look at something called Ethernet protocol. Unless you are on a wireless connection, your computer is likely is plugged into a network using a Cat5 cable (they are typically blue cables with a tabbed connector on the end, although the color doesn’t actually matter). That being the case, there’s a 99.99 percent chance that your computer attaches Ethernet protocol information known as an ‘Ethernet header’ to the front of every packet it sends. Ethernet is a pretty simple protocol used to provide a source and destination address for packets on a local network. It also defines the protocol of the bytes that are following directly after the Ethernet header. Because Ethernet is strictly defined, we know that the first 6 bytes of data will be interpreted as a destination address, the next 6 bytes following will be interpreted as a source address, and the next 2 bytes following will be interpreted as a statement of the protocol type of data following the Ethernet header. So, the Ethernet header is 14 bytes in length and has 3 pieces of important information.
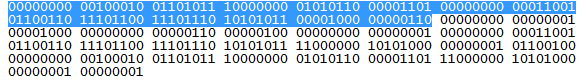
Did you think I had forgotten that this was supposed to be an article about Wireshark at this point? Well, I haven’t! The beauty of Wireshark is that it automatically interprets all of this information from many different protocols and displays it in a hierarchy for you for each packet. If you were looking at the raw data for a packet and wanted to interpret the Ethernet header portion, you’d be examining the blue stream of bits below.
That looks like fun, doesn’t it? Anything look familiar to you? Maybe it’s the fact that there are 14 groups of 8 bits, or 14 bytes outlined in blue. Remember that 14 bytes is the length of the Ethernet header which is placed at the beginning of a packet. Now we’ll look at Wireshark’s interpretation of this information.
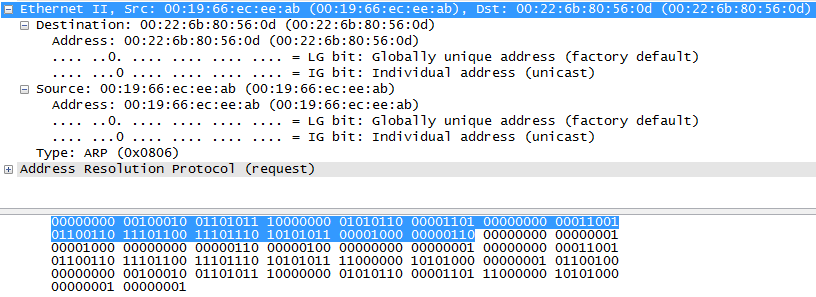
Whoa, hey! Are those English words in that picture? Why yes, they are! As you can see, we have selected and expanded the Ethernet header portion of a packet and we can now see that the destination address is “00:22:6b:80:56:0d”, the source address is “00:19:66:ec:ee:ab”, and the type of protocol that is coming up next in the packet is ARP or Address Resolution Protocol.
But Cameron, you might say, that still looks like nonsense to me! How the heck does “00:19:66:ec:ee:ab” tell me anything more than “00000000 00100010 01101011 10000000 01010110 00001101”? Well, honestly, it won’t just yet if you don’t understand what a source and destination address are used for in the Ethernet header and how it is derived into human readable text from the bits themselves. But in the future, when you do know, Wireshark gives you the capability to quickly find this information in every packet.
And remember when I said it takes a lot of 1’s and 0’s for our enjoyment of computer networks? Well, Wireshark can prevent the “needle in a haystack” issue of searching for problematic packets among the thousands or millions that you might capture in a single capture session by providing efficient search options. For example, even if I have captured a million packets in a single capture session and I wanted to find the one packet with a destination address of “00:19:66:ec:ee:ab”, I can create a display filter in five seconds which will allow me to find that packet and analyze its contents. You could create a filter which will show you all traffic to a particular computer, or all traffic for a particular service (port), or all traffic which contains a specific value of a particular protocol, or any combination of these (e.g. all traffic to a computer which is sent to a particular port and contains a particular value), and many, many more.
There are a multitude of other reasons to use Wireshark, but I hope this article has at least piqued your interest. As a student, I found it difficult to relate to the information I was seeing in Wireshark and didn’t realize the potential for learning until after many grueling and tedious Wireshark sessions. Now I love this thing because it actually helps me fix issues.
A final disclaimer about Wireshark: don’t use it on any network that you don’t have explicit, preferably written permission to do so. You can get into some legal trouble or get fired from your job if you aren’t careful about where you capture packets.